Electronic Team, Inc. uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our cookie policy. Click here to learn more.
Reverse engineering is a common practice in many industries. It is the process of duplicating an existing component or product without the help of documentation, computer models or drawings. It involves a number of steps where the reverse engineers attempt to identify the components of the product in question and understand the relationships between those components.
The process of reverse engineering a product often involves a “black box” approach, where various inputs and their related outputs are studied in an attempt to decipher their effect on its functionality. After understanding the basics of how the system works, the next step is to develop an abstract representation of the components and their interactions. Finally, this abstraction is used to physically create a representation of the original system, attempting to fully duplicate its functionality.
Reverse engineering is employed in many fields, such as consumer products, software engineering, chemicals, and electronics. The practice can be a way around patents and proprietary processes that a manufacturer or developer is reluctant to share with competitors. Successful reverse engineering can result in products that are brought to market quickly, without the need for creating designs from scratch.
There are a number of reasons that reverse engineering is used by manufacturers and companies. Here are some of them:
Based on the industry or product you are attempting to reverse engineer, there may be the need to use specialized tools to understand the original item’s functionality in order to proceed.
A case where specialized tools are instrumental in the ability to reverse engineer a product or component is when working with serial and USB ports and devices. Going back to the concept of the “black box”, the primary inputs and outputs of serial and USB devices are streams of data that need to be analyzed in order to determine the component’s function. Reverse engineering of USB ports and devices demands a way to capture these data streams.
Without adequate tools to assist in this analysis, the reverse engineer would have to spend inordinate amounts of time to enact their analysis on USB and serial device and port activity. To properly reverse engineer USB devices and equipment of this type you need reverse engineering software tools that can assist in monitoring and understanding the device’s input and output activity.
If you are attempting to reverse engineer serial or USB devices or applications that use those ports, then these two tools are great additions to your toolbox. Their full compatibility with both 32 and 64-bit versions of Windows make them excellent Windows reverse engineering tools.
Using these software applications will allow you to monitor and capture all serial and USB data transmission, enabling you to study a device’s behavior thoroughly as you strive to reverse engineer it. You will find them indispensable assets in understanding the functionality of the device or process you are attempting to replicate.
Two software applications that can be used as reverse engineering tools are Electronic Team, Inc. Serial Port Monitor and USB Analyzer. These utilities are designed to provide many features to those technicians working with serial and USB devices and can be crucial in the process of serial and USB reverse engineering. Let’s take a look at the features that these applications offer.
Serial Port Monitor is a full-featured utility for working with serial devices and ports.
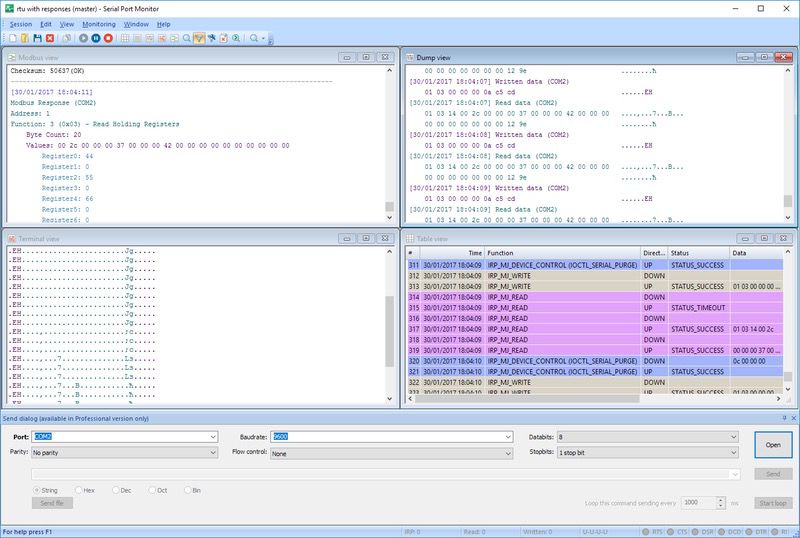
Due to Com Port Monitor, you can connect to any serial port to begin sniffing immediately. This is true even for ports already in use by other applications. Data is captured in real time and presented in a variety of views to facilitate problem resolution. Your data can be sent to a file or the clipboard for further analysis at a later time.
Moreover, data sent and received from devices is recorded on a first-in-first-out basis for easier analysis and can be viewed in 4 ways such as a table, line, dump, and terminal views. Also, this tool fully supports the Modbus protocol.
USB Analyzer (USB Sniffer) includes many features that are required to perform USB reverse engineering tasks.
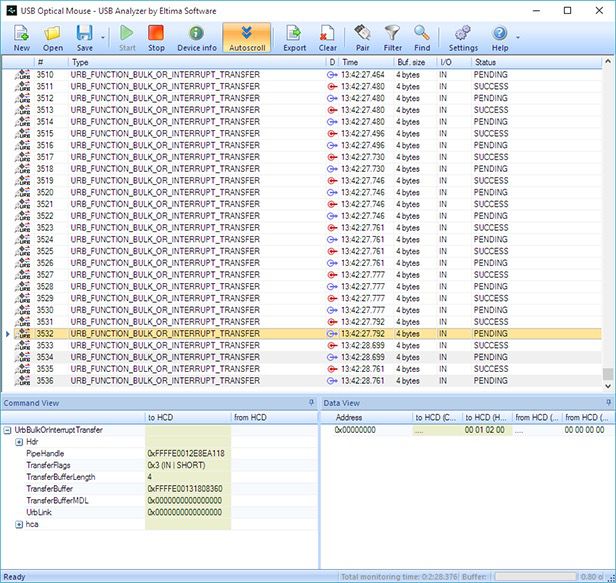
USB Analyzer lets you capture, save and export USB data - IRPs, URBs, IOCTLs, and data transferred through USB hubs are captured and can be saved in binary format or exported to plain text, CSV, XML or HTML. Being a tool made for analysis, the software monitors data in real time from the connected USB devices. That data can be collected as a raw hex dump or can be displayed as a decoded and readable text.